HARDWARE
Computer hardware is the collection of physical elements that constitutes a computer system. Computer hardware refers to the physical parts or components of a computer such as the monitor, mouse, keyboard, computer data storage, hard drive disk (HDD), system unit (graphic cards, sound cards, memory, motherboard and chips), etc. all of which are physical objects that can be touched. In contrast, software is instructions that can be stored and run by hardware.
Software is any set of machine-readable instructions that directs a computer's processor to perform specific operations. A combination of hardware and software forms a usable computing system.
Personal computer

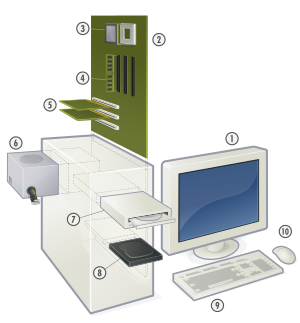
Hardware of a modern personal computer

Inside a custom-built computer: power supply at the bottom has its own cooling fan.
The personal computer, also known as the PC, is one of the most common types of computer due to its versatility and relatively low price.Laptops are generally very similar, although may use lower-power or reduced size components.
Case
The computer case is a plastic or metal enclosure that houses most of the components. Those found on desktop computers are usually small enough to fit under a desk, however in recent years more compact designs have become more common place, such as the all-in-one style designs from Apple, namely the i Mac. Laptops are computers that usually come in a clam shell form factor, again however in more recent years deviations from this form factor have started to emerge such as laptops that have a detachable screen that become tablet computers in their own right.
Power supply
A power supply unit (PSU) converts alternating current (AC) electric power to low-voltage DC power for the internal components of the computer. Laptops are capable of running from a built-in battery, normally for a period of hours.
Motherboard
The motherboard is the main component of computer. It is a large rectangular board with integrated circuitry that connects the other parts of the computer including the CPU, the RAM, the disk drives(CD, DVD, hard disk, or any others) as well as any peripherals connected via the ports or the expansion slots.
Components directly attached to or part of the motherboard include:
- The CPU (Central Processing Unit) performs most of the calculations which enable a computer to function, and is sometimes referred to as the "brain" of the computer. It is usually cooled by a heat sink and fan. Most newer CPUs include an on-die Graphics Processing Unit (GPU).
- The Chip Set, which includes the north bridge, mediates communication between the CPU and the other components of the system, including main memory.
- The Random-Access Memory (RAM) stores the code and data that are being actively accessed by the CPU.
- The Read-Only Memory (ROM) stores the BIOS that runs when the computer is powered on or otherwise begins execution, a process known as Bootstrapping, or "booting" or "booting up". The BIOS (Basic Input Output System) includes boot firmware and power management firmware. Newer motherboards use Unified Extensible Firmware Interface (UEFI) instead of BIOS.
- Buses connect the CPU to various internal components and to expansion cards for graphics and sound.
- The C MOS battery is also attached to the motherboard. This battery is the same as a watch battery or a battery for a remote to a car's central locking system. Most batteries are CR2032, which powers the memory for date and time in the BIOS chip.
Expansion cards
The [expansion card] in computing is a printed circuit board that can be inserted into an expansion slot of a computer motherboard or back plane to add functionality to a computer system via the expansion bus.
Storage devices
Computer data storage, often called storage or memory, refers to computer components and recording media that retain digital data. Data storage is a core function and fundamental component of computers.
Fixed media
Data is stored by a computer using a variety of media. Hard disk drives are found in virtually all older computers, due to their high capacity and low cost, but solid-state drives are faster and more power efficient, although currently more expensive than hard drives, so are often found in more expensive computers. Some systems may use a disk array controller for greater performance or reliability.
Removable media
To transfer data between computers, a USB flash drive or Optical disc may be used. Their usefulness depends on being readable by other systems; the majority of machines have an optical disk drive, and virtually all have a USB port.
Input and output peripherals
Input and output devices are typically housed externally to the main computer chassis. The following are either standard or very common to many computer systems.
Input
Output device
Mainframe computer
A mainframe computer is a much larger computer that typically fills a room and may cost many hundreds or thousands of times as much as a personal computer. They are designed to perform large numbers of calculations for governments and large enterprises.
Departmental computing
In the 1960 and 1970 more and more departments started to use cheaper and dedicated systems for specific purposes like process control and laboratory automation.
Supercomputer
A supercomputer is superficially similar to a mainframe, but is instead intended for extremely demanding computational tasks. As of November 2013, the fastest supercomputer in the world is the Tianhe-2, in Guangzhou, China.
The term supercomputer does not refer to a specific technology. Rather it indicates the fastest computers available at any given time. In mid 2011, the fastest supercomputers boasted speeds exceeding one petaflop, or 1000 trillion floating point operations per second. Super computers are fast but extremely costly so they are generally used by large organizations to execute computationally demanding tasks involving large data sets. Super computers typically run military and scientific applications. Although they cost millions of dollars, they are also being used for commercial applications where huge amounts of data must be analyzed. For example, large banks employ supercomputers to calculate the risks and returns of various investment strategies, and healthcare organizations use them to analyze giant databases of patient data to determine optimal treatments for various diseases.
SOFTWARE
Computer software, or simply software is any set of machine-readable instructions that directs a
computer's processor to perform specific operations. Computer software contrasts with
computer hardware, which is the physical component of computers. Computer hardware and software require each other and neither can be realistically used without the other.
At the lowest level, executable code consists of machine language instructions specific to an individual
processor – typically a
central processing unit (CPU). A
machine language consists of groups of binary values signifying processor instructions that change the state of the computer from its preceding state. For example, an instruction may change the value stored in a particular storage location inside the computer – an effect that is not directly observable to the user. An instruction may also (indirectly) cause something to appear on a display of the computer system – a state change which should be visible to the user. The processor carries out the instructions in the order they are provided, unless it is instructed to "jump" to a different instruction, or interrupted.
Software written in a machine language is known as "machine code". However, in practice, software is usually written in
high-level programming languages that are easier and more efficient for humans to use (closer to
natural language) than machine language. High-level languages are translated, using
compilation or
interpretation or a combination of the two, into machine language. Software may also be written in a low-level
assembly language, essentially, a vaguely
mnemonic representation of a machine language using a natural language alphabet. Assembly language is translated into machine code using an
assembler.
computer software can be divided into:
- Application software, which uses the computer system to perform useful work or provide entertainment functions beyond the basic operation of the computer itself. There are many different types of application software, because the range of tasks that can be performed with a modern computer is so large - see list of software.
- System Software, which is designed to directly operate the computer hardware, to provide basic functionality needed by users and other software, and to provide a platform for running application software. System software includes:
- Operating systems, which are essential collections of software that manage resources and provides common services for other software that runs "on top" of them. Supervisory programs, boot loaders, shells and window systems are core parts of operating systems. In practice, an operating system comes bundled with additional software (including application software) so that a user can potentially do some work with a computer that only has an operating system.
- Device drivers, which operate or control a particular type of device that is attached to a computer. Each device needs at least one corresponding device driver; because a computer typically has at minimum at least one input device and at least one output device, a computer typically needs more than one device driver.
- Utilities, which are computer programs designed to assist users in maintenance and care of their computers.
- Malicious Software or Malware, which are computer programs developed to harm and disrupt computers. As such, malware is undesirable. Malware is closely associated with computer-related crimes, though some malicious programs may have been designed as practical jokes.